Network Security
In a stark reminder of the persistent threats facing enterprise infrastructure, Cisco has issued emergency security updates to address a critical zero-day vulnerability that is already being actively exploited by malicious actors. The flaw, identified as CVE-2026-20045, affects the company’s widely

The proliferation of smart home devices has quietly transformed the typical household network into a sprawling, unsecured digital landscape where every connected gadget, from your security camera to your coffee maker, can freely communicate with one another. This "flat" network

The relentless pace of cloud adoption has fundamentally altered the security landscape, rendering traditional vulnerability management practices obsolete and leaving many organizations dangerously exposed. In today's dynamic cloud environments, where infrastructure can be deployed and

In an increasingly interconnected world where digital infrastructure forms the backbone of government operations, the state of Texas has drawn a firm line in the sand against potential cybersecurity threats from foreign adversaries. The state recently moved to significantly expand its list of
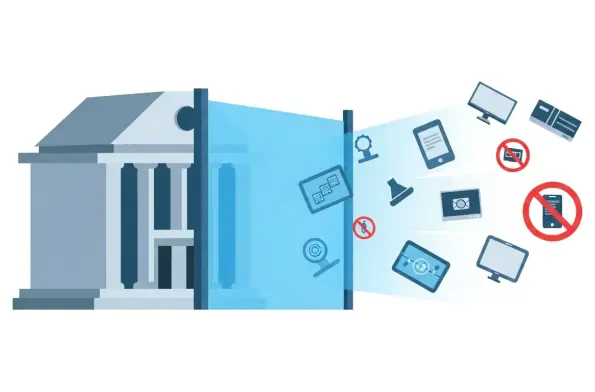
A significant disparity is emerging in the landscape of technological advancement, where the very sectors that stand to gain the most from artificial intelligence are paradoxically the slowest to embrace it. For organizations in highly regulated fields such as banking, healthcare, government, and
A security patch, once applied, is often considered the final word on a vulnerability, but recent events demonstrate that this assumption can create a dangerous blind spot for network administrators. This article investigates a new wave of automated attacks targeting FortiGate firewalls, focusing