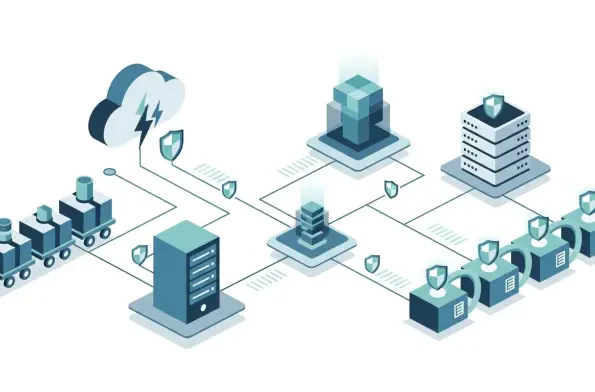
Cyber Risk Management
In the relentless pursuit of enterprise security, the groundbreaking principle of "never trust, always verify" has become a cornerstone of modern cyber defense, yet organizations still grapple with a critical and unanswered question: how can they prove their trustworthiness at any given
The once-private boundary between a user and an artificial intelligence chatbot has been decisively breached by a federal court order, establishing a startling precedent that could transform digital interactions into discoverable legal evidence. In a landmark ruling that reverberates through the

A massive procession recently snaked through the major streets of Calabar, not in protest, but in a powerful display of unity and newfound tranquility, an event that would have been unimaginable just a short time ago. This "Peace Walk," organized by the Cross River State Homeland Safety

The battle against cyber threats has decisively shifted from the server room to the boardroom, fundamentally redefining cybersecurity as a core financial imperative rather than a siloed IT concern. As malicious actors increasingly set their sights on the financial heart of organizations, the Chief

For countless defense contractors operating within the Defense Industrial Base, the mandate for Cybersecurity Maturity Model Certification (CMMC) represents a critical juncture where non-compliance could mean the loss of vital government contracts. The intricate web of controls and documentation

While organizations scrambled to patch the latest software vulnerabilities announced in 2025, threat actors quietly and effectively weaponized a trove of older, forgotten flaws, leading to an unprecedented expansion of CISA's most critical threat list. This research summary delves into the














