Security
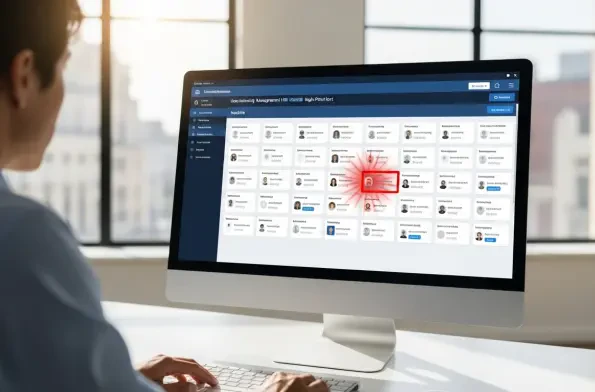
In a landscape where a single data breach now carries an average price tag of $4.45 million, organizations have been forced to confront the harsh reality that traditional security measures, such as basic antivirus software and perimeter firewalls, are fundamentally inadequate. The digital world no

The Central Bank of Nigeria has unveiled a sweeping directive designed to fundamentally reshape the landscape for foreign-issued payment cards, ushering in a new era of enhanced security and operational efficiency for international transactions within the country. Issued via a circular dated

The theoretical power of quantum computing to shatter conventional encryption is rapidly moving from academic discourse to a tangible, long-term risk for all digital infrastructure, with blockchain technology standing at the forefront of this vulnerability. Recognizing that the future of digital
The once-clear boundaries of the corporate network have dissolved into a complex, decentralized ecosystem, making traditional perimeter-based security models fundamentally obsolete. Today's business operations span on-premises data centers, multiple cloud platforms, a diverse array of

A recent in-depth security analysis has uncovered a trio of critical vulnerabilities within PickleScan, a widely-adopted tool for securing Python pickle files and PyTorch models, casting a shadow over the integrity of the AI supply chain. With the rapid integration of machine learning models into

That incredible Christmas discount on a coveted gadget might not be a festive miracle, but rather a meticulously crafted illusion designed by artificial intelligence to empty your bank account. As the holiday season approaches, a new and formidable threat is emerging in the digital marketplace,