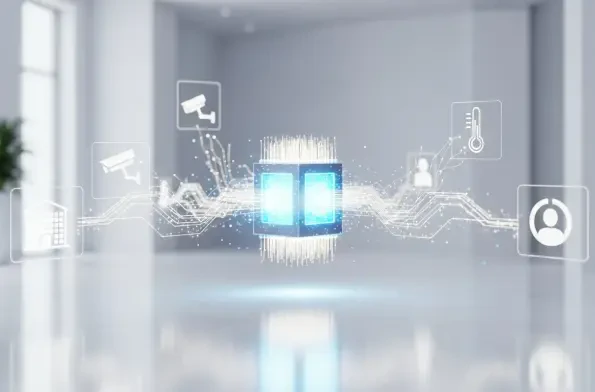
Identity & Access Management
In the rapidly evolving digital landscape, artificial intelligence has officially transcended its role as a futuristic buzzword to become a tangible and powerful weapon, setting the stage for an unprecedented cyber arms race. The consensus among leading security experts is that 2026 will be the

Beyond the Badge Swipe What Does True Security Look Like A sophisticated cyberattack no longer just steals data from a server; it can now unlock the very doors meant to protect a nation's most sensitive assets, turning a digital vulnerability into a tangible physical breach. In this landscape,
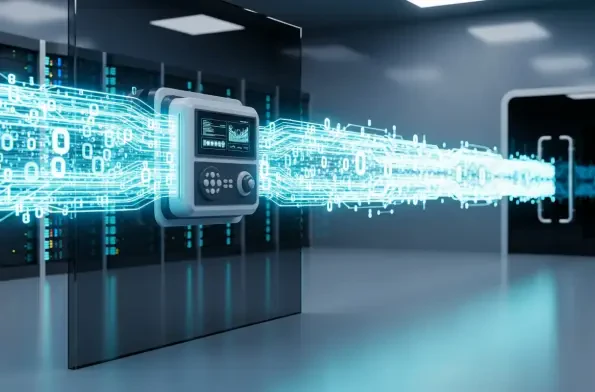
The widespread belief that coordinated global law enforcement efforts had begun to turn the tide against ransomware syndicates has been proven premature, as the threat has not diminished but rather metastasized into a more resilient and efficient form. The ransomware economy underwent a significant

The traditional cybersecurity paradigm, built on the assumption that organizations have a grace period to react between a vulnerability's disclosure and its exploitation, has irrevocably collapsed. What was once a manageable window of days or even weeks for security teams to deploy patches has
The once-fragmented and cumbersome process of verifying one's identity for significant life events has undergone a fundamental and irreversible shift, driven by a confluence of powerful consumer demand and rapid technological innovation. The foundation for this new era was firmly established

The proliferation of advanced security tools across corporate networks has created a dangerous paradox where investment in defense technology is soaring, yet the frequency and impact of successful cyber incidents continue to rise unabated. This reality signals a critical inflection point for the