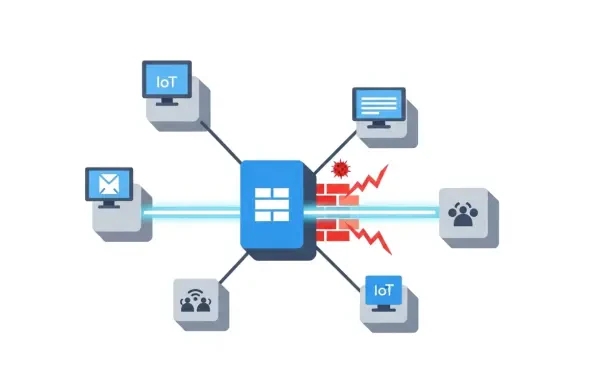
Emerging Threats
In an ironic twist that highlights the fragile operational security within the cybercriminal underworld, a prolific hacker specializing in data theft recently became a victim of the very same tactics they employed against countless others. Security researchers have successfully turned a popular

The very tools designed to simplify IT management and provide remote support are now being systematically turned against organizations, creating a powerful and often invisible backdoor for sophisticated cybercriminals. This alarming trend signifies a critical shift in the threat landscape, where

The simple act of pointing a smartphone camera at a pixelated square to access information has become so commonplace that its potential as a sophisticated tool for cyber espionage is often dangerously overlooked. This ubiquitous convenience, found on everything from restaurant menus to payment

The silent expansion of cyber threats into the sprawling digital cities of modern cloud infrastructure has found its newest and most formidable architect in a malware framework known as VoidLink, signaling an urgent and necessary evolution in defensive strategies. Security analysis of this emerging

The very digital infrastructure that powers modern commerce and innovation has become the most contested and valuable territory for a new generation of sophisticated cybercriminals. As organizations finalize their rapid migration to cloud services, embracing the agility of containers, Kubernetes,
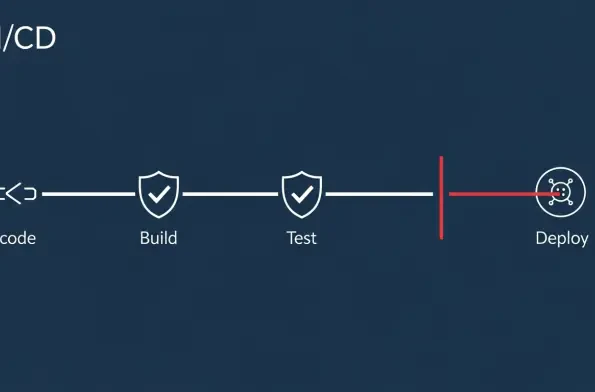
A highly sophisticated cyber-threat group has demonstrated a dramatic escalation in its campaign tactics, rapidly evolving from manual probing to hourly automated attacks against global enterprise infrastructure. An extensive analysis of the group’s command-and-control server logs from March t