Advanced Threat Protection
A highly sophisticated cyber-threat group has demonstrated a dramatic escalation in its campaign tactics, rapidly evolving from manual probing to hourly automated attacks against global enterprise infrastructure. An extensive analysis of the group’s command-and-control server logs from March t
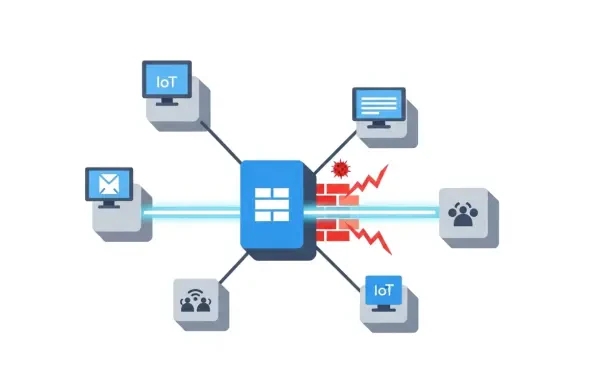
The sense of security that often accompanies owning a premium smartphone was recently challenged when Apple issued an urgent warning to its global user base of approximately 1.8 billion individuals. This alert was not about a common virus or a phishing scam, but a far more insidious threat:

The once-fragmented and cumbersome process of verifying one's identity for significant life events has undergone a fundamental and irreversible shift, driven by a confluence of powerful consumer demand and rapid technological innovation. The foundation for this new era was firmly established

In a digital landscape where data breaches are not a matter of if but when, corporate spending on digital defense has transformed from a discretionary budget item into an essential, non-negotiable operational cost. This unwavering commitment to security creates a remarkably resilient and lucrative

An unseen army of digital soldiers is quietly operating from millions of living rooms and offices across the globe, and the devices they inhabit are not computers or servers but the unassuming Android TV boxes and smart gadgets that have become fixtures of modern life. A sophisticated malware known
The rapid democratization of artificial intelligence is no longer a theoretical concern for futurists but a present and escalating reality for national security agencies worldwide. As advanced technologies become more accessible, the long-standing capabilities gap that once separated state actors














