Advanced Threat Protection
The U.S. Department of Defense is facing a monumental challenge as it races against a critical 2027 deadline to overhaul its cybersecurity infrastructure, a task so vast that traditional human-led methods are proving to be a significant bottleneck. At the heart of this strategic shift is the Zero

The most significant cyber threats targeting the global financial sector are not emerging from the shadows of undiscovered zero-day exploits but are instead being delivered through highly refined, scalable, and ruthlessly efficient criminal enterprises. A forward-looking analysis of the threat

The critical infrastructure that underpins modern digital life, internet service, has once again become a high-profile target for cybercriminals, with US internet service provider Brightspeed now in the midst of a full-scale investigation following alarming claims from a hacking group. The group,
The silent, digital battle for Taiwan's stability escalated dramatically last year, with new evidence pointing to a calculated shift in Beijing's cyber warfare strategy toward crippling the island's most essential services. A comprehensive analysis from Taiwan's National
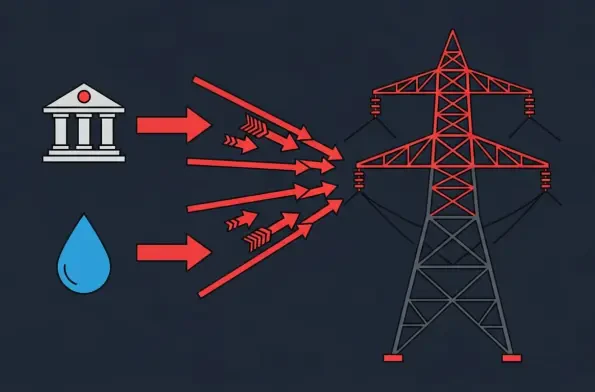
A forgotten router collecting dust in a home office has become a potent weapon for cybercriminals, a scenario now playing out globally as a critical zero-day vulnerability in D-Link hardware highlights a dangerous and growing trend. As millions of legacy devices remain connected to the internet
The very tools designed to streamline operations and connect disparate systems can sometimes harbor hidden doorways for malicious actors, transforming a trusted automation hub into a significant security liability. A newly discovered vulnerability in the n8n platform serves as a stark reminder of