Vulnerability Assessment
Imagine a sprawling digital landscape where businesses operate across multiple cloud platforms, juggling hybrid setups and ever-evolving threats, only to find their security tools lagging behind in a tangle of disconnected alerts and blind spots. This is the reality for many enterprises today as

What happens when a single click on a deceptive email unleashes chaos across cloud systems and software ecosystems? In a world increasingly reliant on digital infrastructure, a new menace has emerged, striking at the heart of open-source platforms and major cloud providers. Named after a legendary

Imagine a water treatment plant suddenly going offline, not due to a mechanical failure, but because a group of hacktivists has defaced its digital interface with political messages. This isn’t a far-fetched scenario but a growing reality in the world of cybersecurity, where industrial control s

I’m thrilled to sit down with Malik Haidar, a seasoned cybersecurity expert who has spent years on the front lines defending multinational corporations against sophisticated cyber threats. With a sharp focus on analytics, intelligence, and security, Malik brings a unique perspective by blending b

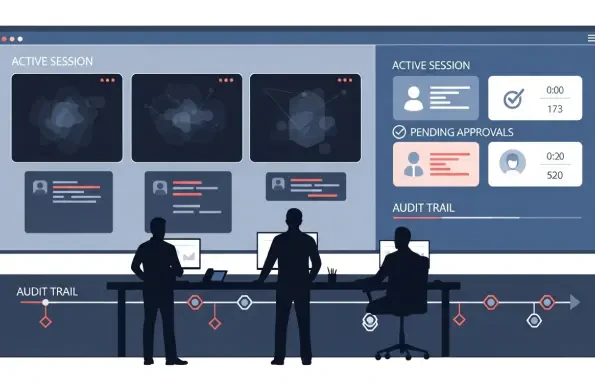
Insider incidents were climbing even as audit scrutiny tightened and workforces spread across clouds, contractors, and home offices, creating a dilemma that looked unsolvable without sacrifice. Security leaders felt pushed to choose between oversight and privacy, between control and speed, and
Security teams counting on clean, high‑volume telemetry suddenly faced a stark reminder that the pipeline itself can become the point of failure when the agent at its core is exploitable and ubiquitous across cloud estates, Kubernetes clusters, and SaaS backbones. Researchers uncovered critical f














