Vulnerability Assessment
The familiar confirmation prompt asking "Are you sure you want to proceed?" has long stood as a reassuring final checkpoint between a user's intent and an AI's action, but a new class of attack now turns that very safeguard into a sophisticated trap. A novel technique detailed

The very digital infrastructure designed to support global commerce and government services is being methodically transformed into a weaponized network by sophisticated threat actors, turning an organization's own assets against others. This escalating trend represents a formidable shift in

A massive data breach has cast a harsh spotlight on the fragile nature of digital privacy, exposing the deeply personal viewing habits of millions of Pornhub Premium users and igniting a firestorm of accusations between the companies involved. The incident centers on the alleged theft of an

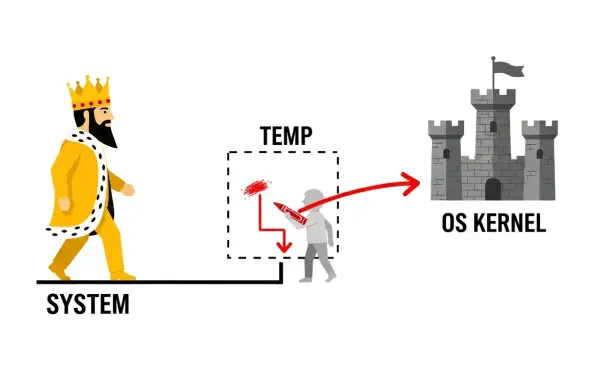
Introduction A seemingly harmless software uninstallation process can become the unlocked back door for an attacker, a reality recently underscored by a critical vulnerability discovered within the widely used JumpCloud platform. The platform, a cornerstone of IT management for thousands of
The relentless cascade of high-profile security breaches throughout 2025 transformed the global conversation around digital risk, solidifying the year as a watershed moment for cybersecurity. An unprecedented volume of sophisticated intrusions targeted major enterprises and household brands,

The administrative tools that system administrators rely on for daily operations are built on a foundation of trust, where elevated permissions are granted to perform necessary tasks efficiently and securely. However, a recently discovered vulnerability in JumpCloud Remote Assist for Windows,