Threat Intelligence
The digital equivalent of decommissioning emergency sirens has just occurred across the federal government, marking a quiet yet profound evolution in the nation's cybersecurity defense posture. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has officially closed 10 Emergency
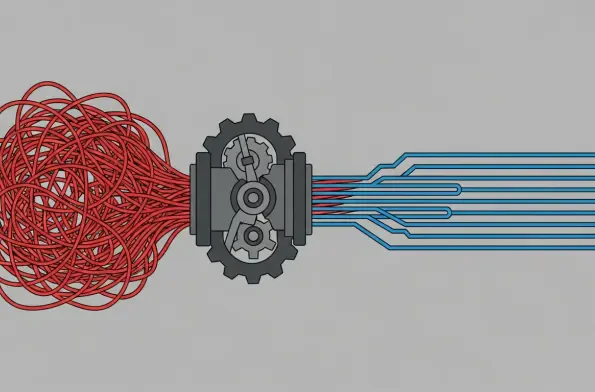
The digital landscape has evolved into a complex and treacherous battlefield where the lines between state-sponsored espionage, organized crime, and opportunistic exploitation have become dangerously blurred. A new paradigm of threat has emerged, one not defined by isolated hackers but by an

The digital clock of a modern enterprise does not just measure productivity; it now ticks down the minutes and millions lost while recovering from an inevitable cyber-attack, a period of downtime that can quickly escalate into an existential crisis. In this landscape, cyber resilience—the ability t

A digital attack from halfway around the world can cripple a nation's infrastructure, a reality underscoring the borderless nature of modern security threats. In this ecosystem, international collaboration is a strategic necessity. However, a major U.S. policy shift now raises fundamental

The rapid acceleration of digital transformation initiatives has irrevocably shattered the traditional concept of a defensible corporate perimeter, leaving organizations to grapple with a new, far more complex security reality. This new landscape is defined not by firewalls and internal endpoints,

Organizations that rely heavily on the n8n platform to automate and connect daily operational tasks must now urgently assess their system's security posture following the discovery of a severe vulnerability. A recently published analysis has brought to light a critical authenticated remote














