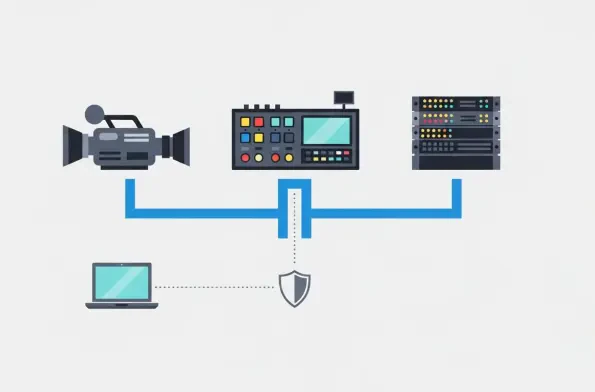
Security Architecture
The traditional cybersecurity paradigm, built on the assumption that organizations have a grace period to react between a vulnerability's disclosure and its exploitation, has irrevocably collapsed. What was once a manageable window of days or even weeks for security teams to deploy patches has
The once-fragmented and cumbersome process of verifying one's identity for significant life events has undergone a fundamental and irreversible shift, driven by a confluence of powerful consumer demand and rapid technological innovation. The foundation for this new era was firmly established

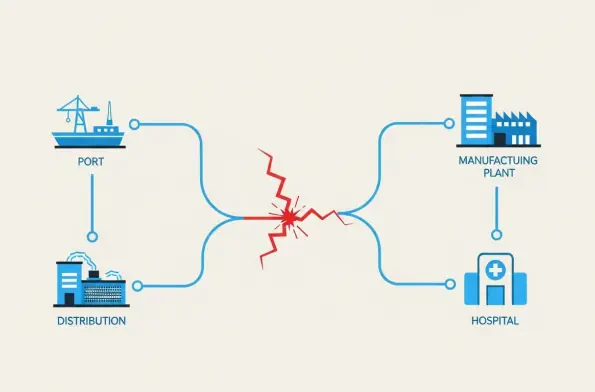
While national conversations about supply chain security often center on tangible disruptions like manufacturing bottlenecks, geopolitical tensions, and natural disasters, an equally potent and far more insidious threat now operates in the digital shadows. Malicious actors, ranging from
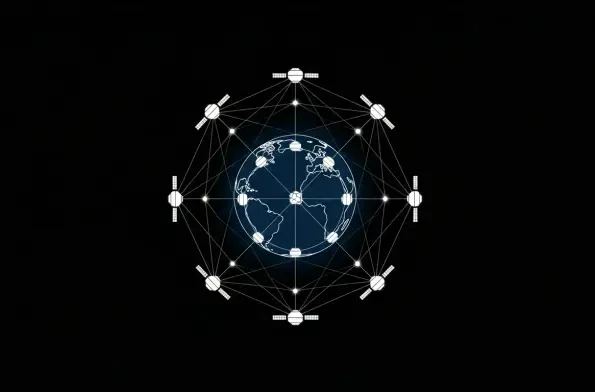
In the increasingly crowded and contested domain of Low-Earth Orbit, where thousands of satellites and pieces of debris travel at speeds exceeding 28,000 kilometers per hour, the window for responding to a potential threat is measured in minutes, not hours. Recognizing this critical vulnerability,
The digital equivalent of decommissioning emergency sirens has just occurred across the federal government, marking a quiet yet profound evolution in the nation's cybersecurity defense posture. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has officially closed 10 Emergency
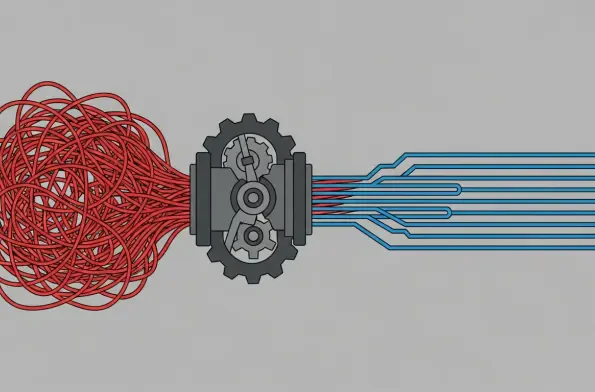
The unforgiving nature of live broadcasting, where a single dropped frame can disrupt an experience for millions, has long relied on a security model of physical isolation, but this approach has become dangerously obsolete in an interconnected, IP-driven world. While the corporate IT sector has