Security Architecture
The latest major release of the open-source firewall platform, OPNsense 26.1, codenamed "Witty Woodpecker," marks a significant evolution in network security management by introducing a powerful API-driven architecture and a suite of new tools designed for modern IT environments. This
The modern enterprise security landscape often resembles a complex patchwork of specialized tools, each acquired to solve a specific problem, yet collectively creating a fragmented and overwhelming operational reality for security teams. This siloed approach, where endpoint protection, identity

The proliferation of smart home devices has quietly transformed the typical household network into a sprawling, unsecured digital landscape where every connected gadget, from your security camera to your coffee maker, can freely communicate with one another. This "flat" network

The relentless pace of cloud adoption has fundamentally altered the security landscape, rendering traditional vulnerability management practices obsolete and leaving many organizations dangerously exposed. In today's dynamic cloud environments, where infrastructure can be deployed and

A massive chasm is widening in the corporate world, separating organizations that proactively modernize their technological foundations from those that do not, a divide that has become the single most critical determinant of success in leveraging Artificial Intelligence. This is not a matter of
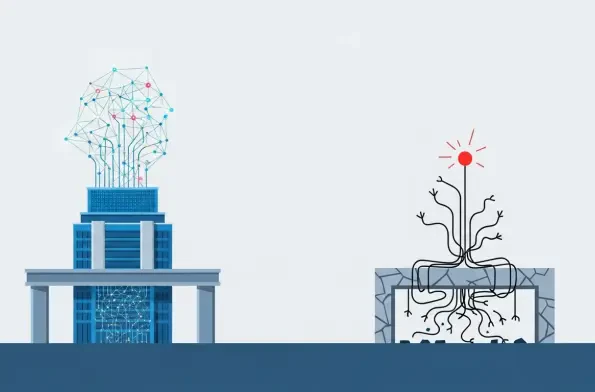
A significant disparity is emerging in the landscape of technological advancement, where the very sectors that stand to gain the most from artificial intelligence are paradoxically the slowest to embrace it. For organizations in highly regulated fields such as banking, healthcare, government, and