Ransomware
The very tools designed to simplify IT management and provide remote support are now being systematically turned against organizations, creating a powerful and often invisible backdoor for sophisticated cybercriminals. This alarming trend signifies a critical shift in the threat landscape, where

The simple act of pointing a smartphone camera at a pixelated square to access information has become so commonplace that its potential as a sophisticated tool for cyber espionage is often dangerously overlooked. This ubiquitous convenience, found on everything from restaurant menus to payment

The silent expansion of cyber threats into the sprawling digital cities of modern cloud infrastructure has found its newest and most formidable architect in a malware framework known as VoidLink, signaling an urgent and necessary evolution in defensive strategies. Security analysis of this emerging

A highly sophisticated cyber-threat group has demonstrated a dramatic escalation in its campaign tactics, rapidly evolving from manual probing to hourly automated attacks against global enterprise infrastructure. An extensive analysis of the group’s command-and-control server logs from March t
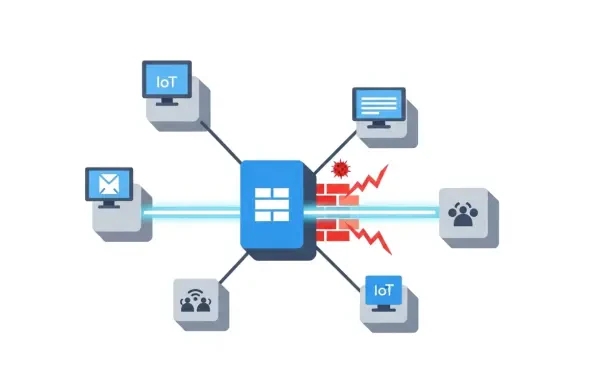
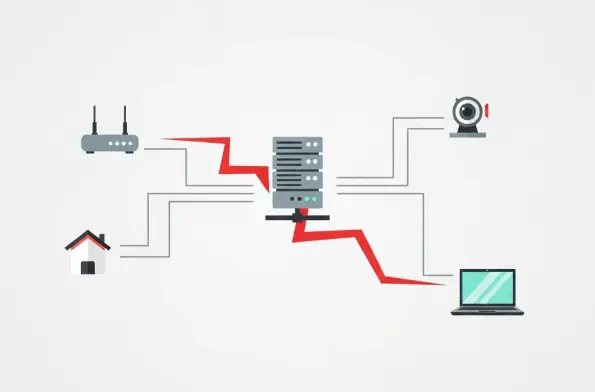
The smart camera monitoring your home or the small business website you manage could be an unwitting soldier in a cybercriminal's army, as a sophisticated threat group is actively hijacking thousands of internet-connected devices to build the powerful RondoDox botnet. This sprawling network of
The long-anticipated inflection point for artificial intelligence in cybersecurity is no longer a future forecast but the present reality, forcing a radical re-evaluation of digital risk across every industry. This year marks a decisive transition away from a phase of AI exploration and theoretical














