Network Security
In an increasingly interconnected global economy, organizations are discovering that their greatest cybersecurity vulnerabilities may not lie within their own digital walls but in the sprawling, complex networks of their suppliers, vendors, and partners. This sobering realization is fueling a

With years of experience defending multinational corporations from digital threats, Malik Haidar has a unique vantage point on the intersection of business strategy and cybersecurity. We sat down with him to dissect the recent Marquis Software Solutions breach, a case that serves as a powerful

The relentless expansion of the hybrid workforce and cloud adoption has pushed IT and security teams to a breaking point, forcing them to navigate a labyrinth of disparate management consoles and security tools. This operational model, often described as a "swivel-chair" nightmare, leads
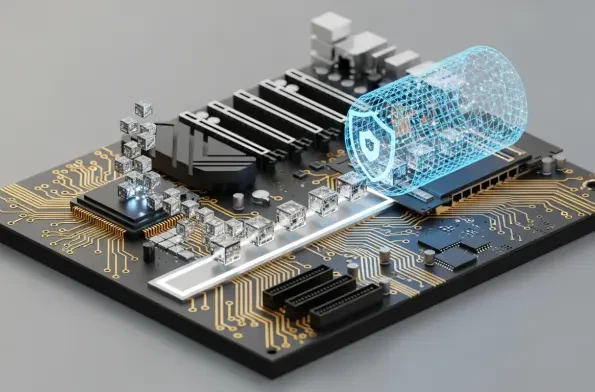
The forthcoming Linux 6.19 kernel is set to introduce a landmark security enhancement that addresses a long-standing and often overlooked vulnerability at the very heart of modern computing: the unencrypted flow of data across internal hardware buses. For decades, the high-speed PCI Express (PCIe)
As of late 2025, the grace period for compliance has conclusively ended, making the European Union's Network and Information Security 2 (NIS2) Directive an enforced reality for businesses across the continent and beyond. This landmark regulation, which officially replaced its 2016 predecessor

As decentralized networks grapple with the monumental challenge of securely onboarding millions of users, the bottleneck of identity verification has become a primary obstacle to growth and mainstream adoption. Addressing this critical juncture, the Pi Network has initiated a significant strategic














