Malware Analysis
The long-standing belief that Apple's ecosystem is a digital fortress, immune to the malware that plagues other platforms, is rapidly crumbling under the weight of new evidence from security researchers. A sophisticated wave of information-stealing malware, or infostealers, is now actively and
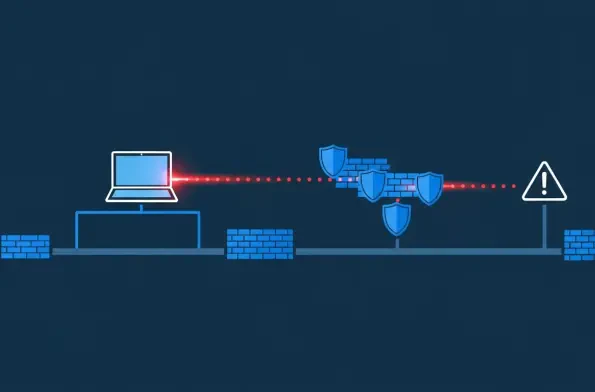
The very tools designed to accelerate innovation and streamline a developer’s workflow have become a new battleground for cyberattacks, transforming trusted development environments into potential gateways for malicious actors. The software supply chain is under siege, and this threat is not a
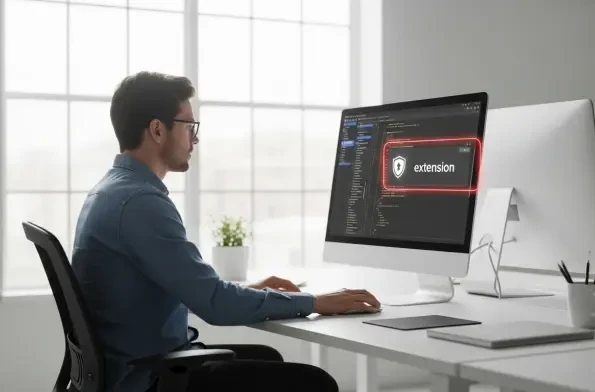
The very tools designed to enhance productivity and streamline digital life are now being weaponized, turning trusted AI assistants into unwitting conduits for sophisticated data theft. A recent security audit has uncovered a widespread campaign targeting users of the popular OpenClaw AI platform,

Introduction: The Rise of Specialized State-Sponsored Cybercrime The shadowy world of state-sponsored hacking is undergoing a profound transformation, moving away from monolithic entities toward highly specialized, mission-driven units. Recent analysis from the cybersecurity firm CrowdStrike on the

In the shadowy world of cyber espionage, a new and deeply disturbing tactic has emerged where the raw grief of a nation is meticulously weaponized to turn activists into victims. A sophisticated campaign, uncovered in January 2026 and codenamed "RedKitten," is targeting Iranian human

A single piece of malicious code, deployed with surgical precision, can simultaneously function as a bank robber and a state secret thief, challenging the long-held distinctions between cybercrime and espionage. The emergence of a sophisticated new malware framework is forcing cybersecurity experts














