Malware Analysis
Imagine a software developer, eager to land a dream job in the blockchain sector, receiving an enticing offer through a professional networking platform. What seems like a golden opportunity quickly turns sinister as a test assignment leads to the download of a malicious npm package, compromising

Imagine installing a simple browser extension to boost productivity, only to discover that this seemingly harmless tool has been quietly stealing your data for years. This chilling reality has struck over 4.3 million users worldwide, ensnared by a cunning cyber threat known as ShadyPanda. Through

Imagine a digital Trojan horse slipping past the most advanced AI guardians of software security, not through brute force, but by whispering sweet nothings to the very tools meant to detect it. This isn't a far-fetched scenario but a stark reality in the latest cybersecurity breach involving a

Imagine a digital battlefield where unseen enemies strike half a million times every single day, targeting devices, networks, and personal data with relentless precision. That’s the stark reality of today’s cyberthreat landscape, where security experts are detecting an average of 500,000 malicious f

In an era where technology underpins nearly every facet of society, the SolarWinds cyberattack emerges as a chilling testament to the destructive potential of software turned into a weapon. This audacious breach, which penetrated deep into the core of U.S. infrastructure via a seemingly innocuous

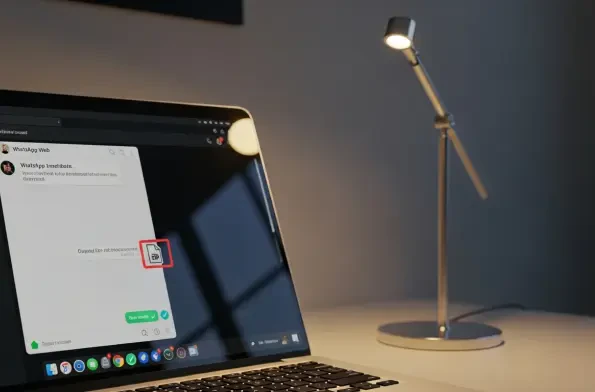
Imagine opening WhatsApp Web to chat with a trusted contact, only to receive a seemingly harmless message with an attachment that, once clicked, unleashes a devastating banking trojan stealing sensitive financial data. This isn’t a far-fetched scenario but the chilling reality of a sophisticated c