Identity & Access Management
Imagine a small rural clinic, bustling with patients seeking care, unaware that their most sensitive personal health information (PHI) is just a click away from falling into the wrong hands. Cyberattacks on healthcare facilities are no longer a distant threat but a stark reality, with breaches

Imagine a sprawling digital landscape where businesses operate across multiple cloud platforms, juggling hybrid setups and ever-evolving threats, only to find their security tools lagging behind in a tangle of disconnected alerts and blind spots. This is the reality for many enterprises today as

Escalating breach costs and headline ransomware incidents have made a hard truth unavoidable for leadership teams and auditors alike: backups that only exist as comfort blankets, untested and ungoverned, cannot be trusted to rescue business operations or pass scrutiny when controls fail and
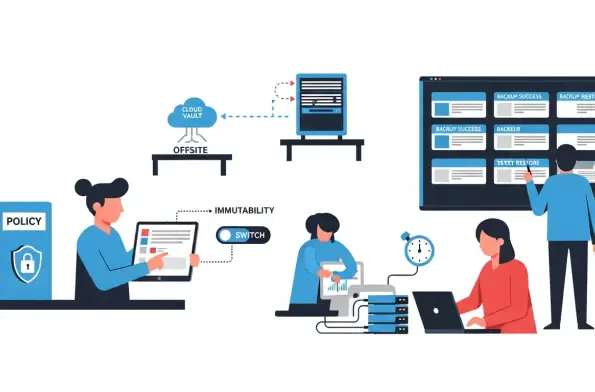
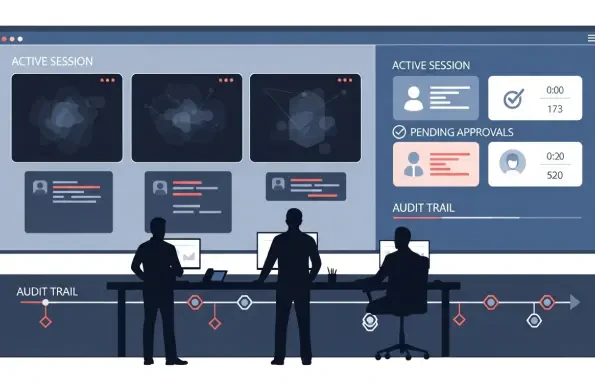
Insider incidents were climbing even as audit scrutiny tightened and workforces spread across clouds, contractors, and home offices, creating a dilemma that looked unsolvable without sacrifice. Security leaders felt pushed to choose between oversight and privacy, between control and speed, and
Why a supplier’s slip can ripple across an airline’s ecosystem News that a vendor breach exposed Iberia customer names, emails, and Iberia Plus IDs jolted security teams because it revealed how familiar details can be weaponized even when passwords and cards stay safe. Several airline CISOs noted th
Malik Haidar has spent the last decade running blue teams inside global enterprises, turning raw threat intelligence into business-aligned action. In this discussion, he opens the playbook behind a fast-moving response to Oracle Identity Manager’s CVE-2025-61757: scoping blast radius across SSO and














