Hacker Groups & Activities
The critical infrastructure that underpins modern digital life, internet service, has once again become a high-profile target for cybercriminals, with US internet service provider Brightspeed now in the midst of a full-scale investigation following alarming claims from a hacking group. The group,
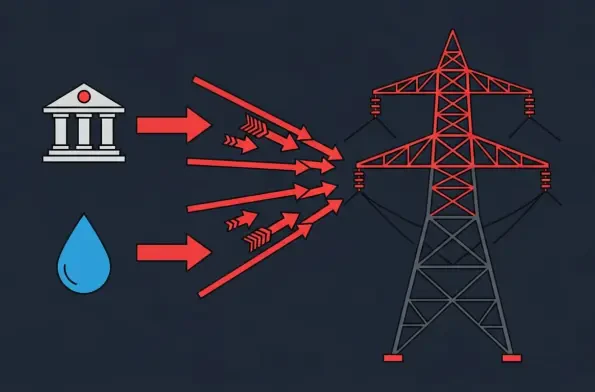
The silent, digital battle for Taiwan's stability escalated dramatically last year, with new evidence pointing to a calculated shift in Beijing's cyber warfare strategy toward crippling the island's most essential services. A comprehensive analysis from Taiwan's National
A groundbreaking analysis from blockchain intelligence firm TRM Labs has meticulously detailed how a significant 2022 data breach at password manager LastPass directly enabled the theft of at least $35 million in cryptocurrency by Russian-linked cybercriminals. The report highlights the severe,

The digital tools that connect millions for daily conversation are increasingly becoming conduits for conflict, blurring the line between personal communication and national security in ways that challenge conventional notions of warfare. An ongoing cyber espionage campaign targeting Ukrainian
While national attention remained intensely focused on traditional pillars of governance such as stabilizing the economy and enforcing physical borders, a far more insidious war was being waged and lost on the digital front. This preoccupation with tangible, conventional threats created a critical

The rapid integration of sophisticated AI into the world's digital town squares has reached a critical inflection point, as a wave of international regulatory actions now targets X and its generative AI, Grok, over the proliferation of synthetic pornographic content. This is not just another