Emerging Threats
In an era where technology underpins nearly every facet of society, the SolarWinds cyberattack emerges as a chilling testament to the destructive potential of software turned into a weapon. This audacious breach, which penetrated deep into the core of U.S. infrastructure via a seemingly innocuous

Imagine a scenario where a seemingly harmless download, something as routine as grabbing a new tool from a trusted open-source repository, turns into a gateway for cybercriminals to steal your most sensitive data. This isn’t a distant hypothetical but a stark reality unfolding in the Web3 and b

In an era where digital threats evolve faster than ever, the cybersecurity landscape stands at a pivotal crossroads with artificial intelligence emerging as both a powerful ally and a potential risk. Imagine a world where cyber attackers use AI to craft sophisticated breaches that outpace

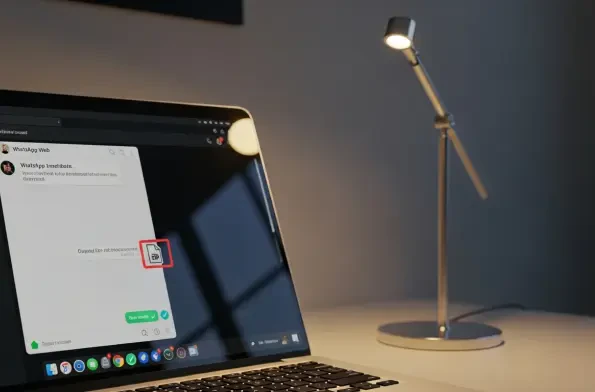
Imagine opening WhatsApp Web to chat with a trusted contact, only to receive a seemingly harmless message with an attachment that, once clicked, unleashes a devastating banking trojan stealing sensitive financial data. This isn’t a far-fetched scenario but the chilling reality of a sophisticated c
In a digital age where data is often called the new oil, a recent cybersecurity incident at Mixpanel, a prominent web and mobile analytics company, has exposed just how vulnerable that resource can be. Announced right before the U.S. Thanksgiving holiday, the breach, detected on November 8, has

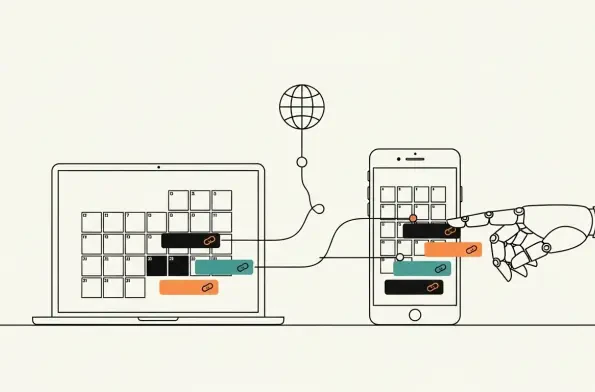
How legitimate calendar subscriptions enable scalable phishing and malware delivery Millions rely on calendar subscriptions for frictionless updates to holidays, school events, sports fixtures, and store promotions, yet the same convenience masks a quiet channel that continuously syncs in the