Cyber Risk Management
Cabin connectivity promised seamless service, but the reality is a crowded publish–subscribe network where dozens of vendors’ devices trade messages in milliseconds while quietly expanding an internal attack surface that traditional defenses do not touch. Transport encryption locks down links, and b

Small businesses with lean teams and tight margins have increasingly found that a single cyber incident can knock out core systems, disrupt sales, and trigger a costly scramble to recover, even when the breach started with nothing more than a phish or a misconfigured account exposed to the

Lead Fifteen point seventy-two terabits per second of hostile traffic hit one Australian cloud endpoint as 3.64 billion packets per second rode the surge, and the page that flood tried to drown never blinked. The blast came from more than 500,000 source IPs, surged in bursts, and still met an

A Knock That Sounds Familiar Two rings, a pause, then a persuasive voice claiming to be “vendor support” with urgent instructions to verify access before the next shift—a script that has fooled seasoned professionals and, this fall, pried open a new entry point at DoorDash through a targeted social

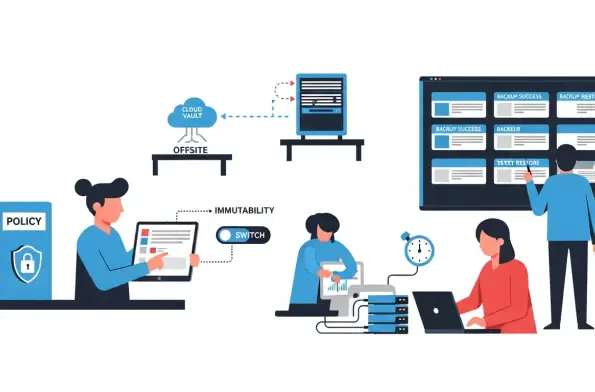
Escalating breach costs and headline ransomware incidents have made a hard truth unavoidable for leadership teams and auditors alike: backups that only exist as comfort blankets, untested and ungoverned, cannot be trusted to rescue business operations or pass scrutiny when controls fail and
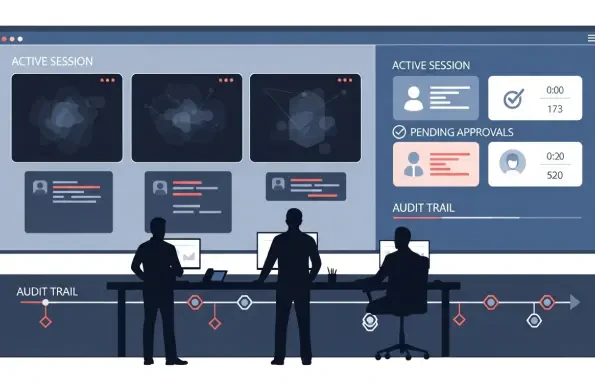
Insider incidents were climbing even as audit scrutiny tightened and workforces spread across clouds, contractors, and home offices, creating a dilemma that looked unsolvable without sacrifice. Security leaders felt pushed to choose between oversight and privacy, between control and speed, and