Cyber Risk Management
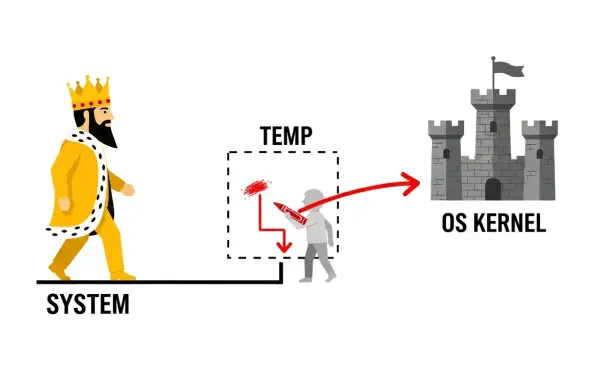
Introduction A seemingly harmless software uninstallation process can become the unlocked back door for an attacker, a reality recently underscored by a critical vulnerability discovered within the widely used JumpCloud platform. The platform, a cornerstone of IT management for thousands of
The relentless cascade of high-profile security breaches throughout 2025 transformed the global conversation around digital risk, solidifying the year as a watershed moment for cybersecurity. An unprecedented volume of sophisticated intrusions targeted major enterprises and household brands,

The familiar click of a metal key turning in a lock is rapidly being replaced by the silent, data-driven precision of digital systems that are fundamentally reshaping how organizations protect their most valuable assets. This evolution from standalone mechanical hardware to intelligent,

The healthcare payer information technology sector is undergoing a fundamental and rapid transformation, with the year 2026 emerging as a critical inflection point for execution and modernization. Survey findings from Black Book Research, involving over a thousand payer IT and administrative

The intricate digital infrastructures that underpin modern society are facing an unprecedented and increasingly sophisticated barrage of threats, forcing a critical re-evaluation of long-held security doctrines. Recent gatherings of top industry professionals have solidified a consensus that the

A threat actor's decision to model a malware component after the classic mobile game 'Snake' perfectly encapsulates the bizarre and creative evolution of modern cyber warfare, where nostalgia and espionage unexpectedly intersect. This is not merely a gimmick; it is a clear signal of