Advanced Threat Protection
For years, the smart lock industry dangled the promise of a truly keyless future, one where your very presence would be enough to grant you access to your home. While the introduction of features like PIN codes and remote app control successfully untethered users from physical keys, the

In a digital landscape where trust is an increasingly scarce commodity, the decision by ad-blocking specialist AdGuard to open-source its proprietary Virtual Private Network protocol has sent a clear message to the entire privacy sector. The protocol, newly christened TrustTunnel, represents a

Oracle has begun the year with a sweeping security initiative, releasing a massive Critical Patch Update (CPU) that addresses a staggering 337 new vulnerabilities across its extensive portfolio of enterprise software. This initial quarterly update for 2026 tackles approximately 230 distinct Common

The seemingly harmless coding challenge presented during a remote job interview has now become one of the most insidious vectors for state-sponsored espionage and financial theft, transforming the global developer community into an unwitting cyber battlefield. This shift marks a significant

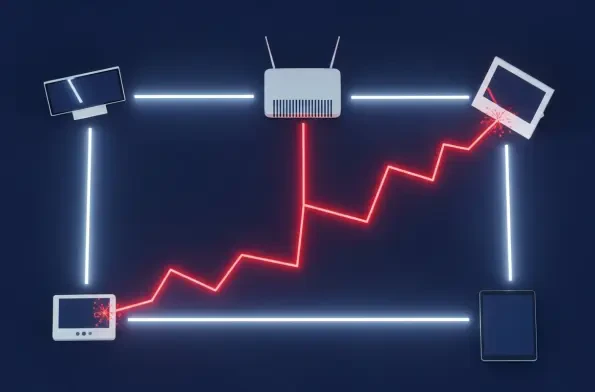
A deeply troubling security advisory has revealed the emergence and explosive growth of a sophisticated malware operation that shatters the foundational assumption of home network security, proving that devices operating behind a standard router are no longer inherently safe from external threats.
In the rapidly evolving digital landscape, artificial intelligence has officially transcended its role as a futuristic buzzword to become a tangible and powerful weapon, setting the stage for an unprecedented cyber arms race. The consensus among leading security experts is that 2026 will be the














