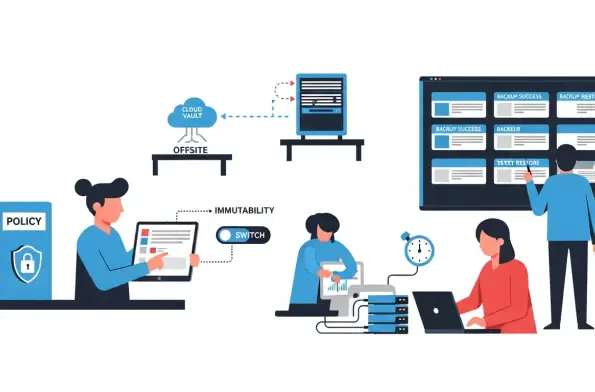
Escalating breach costs and headline ransomware incidents have made a hard truth unavoidable for leadership teams and auditors alike: backups that only exist as comfort blankets, untested and ungoverned, cannot be trusted to rescue business operations or pass scrutiny when controls fail and evidence is demanded on deadline. Organizations that treat backup as an operational control inside the security management system—not a background task—can show how decisions, configurations, and outcomes align with risk, continuity targets, and privacy obligations. That means linking recovery objectives to business impact, enforcing strong security on backup platforms, proving isolation from attack paths, and collecting artifacts that withstand an audit. The shift is cultural as much as technical: backup becomes measurable assurance that data is protected, recoverable, and handled according to policy, not a vague promise to restore someday.
Foundations
Why Backups Are a Control, Not Just a Failsafe
Backups function as a control only when governed by policy, designed from risk, and proven with results tied to explicit Recovery Time and Recovery Point Objectives. Establishing those targets begins with a business impact analysis that ranks systems by criticality, maps tolerable downtime and data loss, and translates those constraints into schedules, storage tiers, and replication patterns. Traceability is nonnegotiable: document policy revisions, backup job definitions, and infrastructure changes, and maintain a changelog that shows who approved what, when, and why. When a restore fails or an objective is missed, treat it as a control exception, analyze root cause, and record corrective actions in the same workflow used for production incidents and problem management.
Under attestation and certification regimes, a backup that cannot be restored on time looks like a breakdown in governance, not just a technical hiccup. SOC 2 examiners evaluating Availability judge whether the control set supports commitments to customers, such as defined service levels or recovery windows, while ISO/IEC 27001 auditors verify that backup is embedded in the ISMS and aligned with continuity planning. That is why capacity monitoring and alerting matter as much as job success rates; a full repository or misconfigured retention can quietly sabotage recoverability. Treat backup telemetry like production monitoring: track success, duration, throughput, dedupe efficiency, and anomaly signals, then retain logs long enough to cover the audit period and trend analysis.
SOC 2 and ISO 27001 Essentials
The practical path forward is to translate abstract clauses into actions that leave a durable evidence trail. For SOC 2, the mandatory Security criterion interacts with Availability, Processing Integrity, Confidentiality, and Privacy; backup touches each when executed as a cohesive control. Encryption governs confidentiality, access control governs security, restore testing demonstrates availability and processing integrity, and retention rules intersect with privacy. For ISO/IEC 27001, build backup into risk treatment, change management, and business continuity, and show how policies drive procedures and tool configurations. Surveillance auditors expect to see not just a written policy, but a loop of measurement and continual improvement.
Timelines reinforce the need for sustained discipline. SOC 2 reports assess design and operating effectiveness across the period, so evidence must span the entire window with consistent artifacts. ISO 27001 certification involves ongoing surveillance, meaning last-minute cleanups rarely satisfy assessors who expect stable processes, not sprints before audit day. Choose controls that are auditable by design: platforms with immutable storage, role-based access, integrated reporting, and test-restore automation reduce manual burden while generating screenshots, logs, and dashboards that document reality. The throughline is verifiable governance—policies prove intent, configurations prove implementation, and logs prove execution.
Designing Compliant Backups
Policy and Planning
A credible backup policy reads like a contract with the business: it specifies RTO and RPO per system, explains rationale based on risk, and defines how changes are requested, reviewed, and approved. Embed links to business impact analyses and disaster recovery plans, and require inventory mapping so each application and dataset has an assigned protection method and retention. Capacity management belongs in policy because it directly influences success rates; define thresholds for storage utilization, alerting, and expansion procedures to avoid silent failures. Include testing cadence, reporting expectations, and exception handling so there is a predictable way to address edge cases and waivers.
Governance is only real if it can be traced, so maintain a living register of backup jobs, associated assets, locations, encryption states, and retention policies. Tag each entry with control owners, approvers, and change dates to make audit walkthroughs fast and precise. When assets move to new cloud regions, undergo migration, or change classification, enforce a change process that reviews RTO/RPO alignment and adjusts plans. This is where SOC 2 Availability and Security intersect with ISO 27001’s policy and continuity controls: decisions must be deliberate, justified, reviewed, and visible. By aligning documentation, inventory, and monitoring, organizations create a single source of truth that turns backup from tribal knowledge into an accountable control.
Security and Access Control
Securing the backup itself protects the last line of defense. Encrypt data in transit with modern protocols and at rest with managed keys or hardened vaults, documenting cipher suites, key rotation, and custody. Apply separation of duties so no single administrator can alter retention, disable immutability, and delete data without oversight. Force multifactor authentication for console access and API operations, and restrict network exposure to administration endpoints through allowlists and private connectivity. Monitoring should be tuned to catch privilege escalations, policy changes, and unusual data movement, with alerts routed to incident response just like production signals.
Role-based access control translates policy into enforceable boundaries: define roles for backup operators, security reviewers, and auditors, and assign least privilege consistent with responsibilities. Regularly recertify access to ensure users still need rights, and log all administrative actions with immutable timestamps. SOC 2 examiners look for logical access controls and proof that authentication and authorization work in practice; ISO 27001 auditors expect secure authentication and access restriction over information assets, including backup repositories. Screenshots of role maps, key management settings, and immutability toggles, combined with logs and tickets that show who approved changes, create the audit narrative that security was designed and operating effectively.
Operating and Proving Effectiveness
Reliable Runs and Ransomware Resilience
Operations are the proving ground where intent meets outcome. Schedule backups to meet RPOs while minimizing business impact, then monitor job completion, duration, and data volumes for drift. Unexpected growth can cause windows to slip, so capacity planning and performance tuning should be routine. Track anomalies such as sudden spikes in change rates, which may suggest encryption events or mass deletions, and integrate signals with the SIEM for correlation. When failures occur, use documented runbooks to re-queue jobs, escalate incidents, and capture postmortems that feed continual improvement. These practices directly underpin assertions around SOC 2 Availability and the ISO 27001 backup control.
Modern threats demand stronger measures than traditional tape rotation. Immutability prevents alteration and deletion for a set window, insulating recovery points from malware and insider abuse. Logical or physical separation—whether object-lock, backup network isolation, or true air gapping—reduces the chance that a compromise spreads to the last resort. Replication across regions or providers adds survivability but must be governed by data residency and contractual constraints. Test failover workflows that assume production identity services are impaired, validating that credentials, DNS, and dependencies are available during stress. When resilience is engineered into operations, evidence of success becomes routine byproduct rather than a scramble before audit.
Testing, Integrity, Retention, and Audit Evidence
Restores close the loop by demonstrating that data can be recovered within defined objectives and remain usable. Run periodic test restores for representative systems, capturing start and end times, volumes, and any deviations from plan. Validate application consistency, not just file presence, by checking logs, checksums, and functional smoke tests that exercise key workflows. Document outcomes, raise corrective actions, and track them to closure; auditors weigh not just the pass rate, but the feedback loop that improves reliability. Integrity checks serve Processing Integrity by ensuring restored data is accurate and complete, while metrics on success reinforce Availability claims.
Retention and deletion practices bridge compliance and privacy. Codify retention periods by data class, map them to legal and contractual obligations, and configure them in tooling with protective locks where supported. Implement auditable deletion for expired data and for subject-driven requests, ensuring backup repositories do not undermine minimization commitments. Maintain a package of evidence that includes policies, role assignments, platform screenshots, architecture diagrams showing isolation paths, and logs from backup tools, SIEM, and restore tests. Conduct internal audits that simulate external requests to verify readiness and identify gaps. By the time auditors arrived, the program had already demonstrated, with artifacts and outcomes, that backups were secure, available, tested, and governed—positioning the next steps toward automated reporting, expanded immutability coverage, and tighter linkage between risk changes and protection updates.