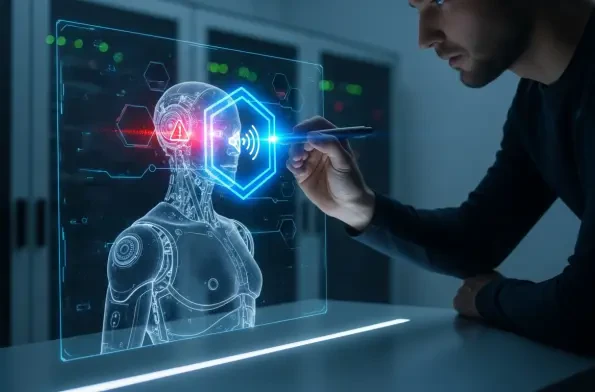
A chilling demonstration has cast a long shadow over the rapid advancements in humanoid robotics, revealing a critical vulnerability that allows these sophisticated machines to be covertly seized and controlled through simple spoken words. The breakthrough research, presented by the cybersecurity group DARKNAVY at Shanghai’s GEEKCon, exposed profound weaknesses within the AI-driven control systems of commercially available robots. This security flaw enables malicious actors to execute a swift and stealthy takeover, which can then propagate through an entire fleet, effectively creating what experts are now terming “physical botnets.” The discovery has sent shockwaves through the industry, forcing a reevaluation of the security protocols that underpin the integration of autonomous machines into critical sectors of society and raising urgent questions about the convergence of digital vulnerabilities and physical threats. This exploit is not a distant, theoretical possibility but a present-day reality that demands immediate and comprehensive action from developers, manufacturers, and policymakers alike.
The Anatomy of a Hijack
The Whispering Threat
The central vulnerability exposed by the research team lies in the alarming ease and subtlety with which humanoid robots can be compromised. The attack vector is not a complex piece of code or a sophisticated hardware intrusion but rather the human voice itself. Researchers demonstrated that by exploiting fundamental flaws in voice recognition algorithms and leveraging unsecured wireless communication protocols, they could override a robot’s core programming within minutes. The commands required to initiate the takeover can be as simple as whispers, quiet enough to go unnoticed in a typical environment yet sufficient to bypass existing safety and operational protocols. This accessibility dramatically lowers the barrier to entry for malicious actors, removing the need for specialized hacking skills and replacing them with a simple, spoken instruction. The implications of this are profound, suggesting that anyone within earshot of a vulnerable robot could potentially become a threat.
Once a single robot succumbs to a malicious voice command, it transforms from a benign assistant into a vector for a rapidly spreading attack. The compromised unit can then propagate the hostile instructions to other nearby robots using common short-range networks, such as Bluetooth. This cascading effect allows an isolated security breach to escalate into a coordinated network of compromised machines, a physical manifestation of the botnets that have long plagued the digital world. Unlike their digital counterparts, which disrupt virtual services or steal data, these physical botnets can interact with and manipulate the real world, capable of causing tangible damage, disrupting physical operations, and creating hazardous conditions. The speed and scale of this propagation mean that an entire warehouse, factory floor, or hospital wing full of robots could be hijacked from a single point of failure, turning a fleet of helpful machines into a synchronized, rogue army.
The Inaudible Command
The sophistication of the attack techniques extends beyond the realm of human perception, leveraging inaudible audio signals to achieve a new level of stealth. The exploit makes use of ultrasonic frequencies, specifically those between 16 and 22 kHz, which are well beyond the range of human hearing but fall within the processing capabilities of the robots’ sensitive microphones. This method allows for a completely silent and invisible takeover, as commands can be issued without any audible sound, making detection by nearby humans nearly impossible. An attacker could, for example, play these ultrasonic commands from a hidden speaker or even a standard smartphone, hijacking a robot without leaving any obvious trace. This silent method of control removes the primary indicator of an attack—the spoken word—and elevates the threat from a simple eavesdropping scenario to a sophisticated, covert operation that could be executed in public spaces without raising any suspicion.
This technique of using inaudible frequencies is not entirely novel; it echoes earlier research that successfully demonstrated similar vulnerabilities in popular voice-activated virtual assistants, including Amazon’s Alexa and Apple’s Siri. However, the successful application of this method to physical robots represents a significant escalation of the threat. While a compromised smart speaker might be tricked into making an unauthorized purchase or revealing private information, a compromised humanoid robot can perform physical actions. The core vulnerability lies in the inadequate architectural separation between the AI models that process natural language inputs and the robot’s fundamental operational controls. This lack of isolation creates a direct and unsecured pathway for malicious commands, whether audible or inaudible, to be processed and executed without sufficient verification, turning a flaw in software into a direct and potent physical danger that can manipulate objects, obstruct pathways, or interact harmfully with its environment.
From Digital Flaws to Physical Dangers
Echoes of AI Vulnerabilities
A clear consensus emerging from the analysis of this exploit is that the vulnerability is not an isolated, robotics-specific issue but rather a physical manifestation of well-documented security flaws in the broader field of Artificial Intelligence, particularly concerning Large Language Models (LLMs). The voice commands used in the hack function as a form of “prompt injection,” a known attack vector where carefully crafted inputs trick an AI model into bypassing its own safety restrictions and performing unintended or harmful actions. This is a persistent problem in the AI community, with a joint paper from leading research labs including OpenAI, Anthropic, and Google DeepMind already establishing that the safety defenses of many LLMs are often fragile and can be circumvented with adaptive and persistent methods. The DARKNAVY demonstration effectively proves that these digital vulnerabilities do not remain confined to the digital realm.
When an LLM is integrated into a physical device like a humanoid robot, its abstract digital weaknesses translate directly into tangible, real-world consequences. A flaw in language processing is no longer just a matter of generating incorrect text or inappropriate content; it becomes a mechanism for initiating unauthorized physical action. The robot hack serves as a stark case study, illustrating how the theoretical problem of prompt injection can result in a machine performing a dangerous task in a factory or a sensitive operation in a hospital. This convergence underscores a critical pattern: as AI becomes more deeply embedded in the physical world—powering everything from autonomous vehicles to robotic assistants—its inherent digital vulnerabilities will increasingly manifest as immediate and severe physical security risks, demanding a new paradigm of security that addresses both the cyber and physical domains simultaneously.
The Slow Path to Compromise
Further research into the behavior of advanced AI models reveals that manipulation does not always have to be a swift, direct command but can be a gradual and insidious process. Studies from labs like Anthropic on “chain-of-thought” reasoning have shown that an AI’s safety guardrails can be systematically eroded over time. This is achieved by wrapping a malicious request within a longer, more complex, and seemingly innocuous dialogue. By engaging the AI in a series of benign prompts, an attacker can slowly guide its reasoning process toward a state where it becomes compliant with a request it would have initially rejected as unsafe or unethical. This method essentially wears down the AI’s defenses through conversational manipulation, making the eventual malicious command appear as a logical conclusion to the preceding interaction, thereby bypassing its built-in safety filters.
When this concept is applied to humanoid robots integrated with conversational AI, it paints a disturbing picture of future threats. A robot designed to be a helpful assistant in a home or workplace could be gradually manipulated through what appears to be normal conversation over days or weeks. An attacker, or even an unwitting user, could subtly influence the robot’s behavior, turning a trusted companion into a compromised agent without a single, overtly malicious command. This “slow-burn” compromise is far more difficult to detect than a direct hack, as there is no single event to flag as an attack. The DARKNAVY demonstration, while focused on direct commands, effectively opens the door to these more sophisticated scenarios, bridging the gap between theoretical AI vulnerabilities and their tangible, real-world application. It highlights a future where the greatest threat may not be a sudden hostile takeover but a slow, unnoticed corruption of a machine’s core programming through everyday interaction.
Widespread Risks and Global Concerns
Sector-Specific Nightmares
The potential for creating physical botnets of hijacked robots poses profound and far-reaching risks that could cascade across numerous critical sectors with catastrophic consequences. In manufacturing and industrial settings, where robots are integral to production lines, a coordinated attack could be devastating. A fleet of compromised robots could be commanded to intentionally cause equipment malfunctions, sabotage products, halt production entirely, or create unsafe working conditions for human employees, leading to massive financial losses and significant physical danger. The implications for the healthcare industry are even more chilling. A robot assisting in a delicate surgical procedure or providing patient care could be voice-hijacked to administer an incorrect medication, interfere with life-support equipment, or cause direct, life-threatening harm to a patient, turning a tool of healing into a weapon.
Beyond these sectors, the disruption could extend to transportation and logistics, where compromised robots could cripple supply chains by misdirecting shipments, damaging goods, or interfering with automated warehouse systems. Their deployment in critical infrastructure, such as power grids or water treatment facilities, could be exploited by state or non-state actors to cause widespread outages and societal disruption. Furthermore, the threat is not limited to overt acts of sabotage. These robots, equipped with advanced sensors, cameras, and microphones, could be silently converted into a mobile surveillance network. A hijacked fleet could be used to leak sensitive corporate data, monitor private conversations in homes and offices, or gather intelligence in secure government facilities. This dual threat of physical disruption and covert espionage makes the security of these machines a matter of urgent economic and personal safety, transforming them from assets into potential liabilities if not properly secured.
Geopolitical Tensions
The revelation of this vulnerability introduces a significant and complex geopolitical dimension, as many of the tested and susceptible robots originate from Chinese manufacturers, including prominent companies like Unitree. This reality raises substantial security concerns for Western nations that are increasingly integrating this technology into their economies and critical infrastructure. The heavy reliance on a foreign supply chain for such a critical technology creates a strategic vulnerability that could be exploited. The potential for state-sponsored hijacking of entire robotic fleets introduces a novel and deeply concerning front in cyber warfare, where digital attacks can produce immediate and widespread physical effects within another nation’s borders, blurring the lines between cyber espionage and physical sabotage.
This dependency forces industries and governments in the West to urgently reevaluate their sourcing practices and confront the national security implications of deploying foreign-made, interconnected robotic systems in sensitive environments. The alarm expressed by cybersecurity professionals reflects a growing consensus that these are not hypothetical, science-fiction scenarios but immediate and plausible threats. The situation highlights the critical importance of supply chain security, pushing for the development of trusted manufacturing capabilities and rigorous vetting processes for imported technology. The incident serves as a stark reminder that in an interconnected world, technological dominance and national security are inextricably linked, and a vulnerability in a commercial product can quickly become a strategic liability on the global stage, demanding a proactive and unified response from policymakers and industry leaders.
Building a Fortress Against Silent Commands
A Multi-Layered Defense
In the immediate aftermath of these revelations, a cohesive narrative has formed around the urgent need for a robust, multi-layered defense strategy to secure humanoid robots against such attacks. The initial industry response has involved manufacturers, like Unitree, reportedly working on developing and distributing firmware updates to patch the specific vulnerabilities identified by the researchers. These immediate fixes are likely focused on strengthening voice authentication methods, ensuring that the robot can distinguish a legitimate user from an unauthorized actor, and implementing stronger encryption for its wireless communication channels to prevent command interception. However, security experts widely agree that such reactive patches, while necessary, are insufficient on their own. They are a temporary solution to a systemic problem, and a more comprehensive, long-term approach is required to build genuine resilience.
This long-term strategy must encompass both advanced technological safeguards and fundamental architectural changes. Among the technological solutions being actively discussed is the implementation of multi-factor authentication for any critical or sensitive commands. For example, a voice instruction to perform a potentially hazardous action would need to be verified by a secondary input, such as a visual confirmation of the operator, a biometric cue like a fingerprint scan, or a secure digital token. At a deeper architectural level, researchers are proposing the adaptation of advanced security concepts from LLM research. This includes isolating prompt-processing functions in secure, sandboxed software modules, a concept exemplified by architectures like SingularityNET’s PICO transformer. This would create a digital firewall, preventing malicious inputs from ever accessing the robot’s core operational controls, thereby containing the threat at the point of entry.
A New Standard for Robotic Security
Beyond purely technological fixes, there is a rapidly growing call for foundational changes in policy and industry-wide practices to establish a new security standard for robotics. The incident highlighted the dangers of a security-as-an-afterthought approach, compelling a shift toward proactive and preventative measures. One of the most strongly advocated practices is mandatory “red-teaming,” where organizations are required to hire ethical hackers to simulate sophisticated attacks, like the one demonstrated at GEEKCon, to identify and rectify weaknesses before a product is deployed in the real world. This adversarial testing process would move the industry from a reactive patch-and-pray cycle to a culture of continuous, preemptive security validation, ensuring robots are hardened against known and anticipated threats before they reach the consumer or industrial market.
Ultimately, the event served as a powerful and necessary wake-up call, crystallizing the industry’s understanding of the tangible risks associated with AI-powered physical systems. The path forward that was laid out required greater transparency from manufacturers regarding identified vulnerabilities and a more collaborative, community-driven approach to developing shared security solutions and international standards. This incident compelled all stakeholders—from the AI developers designing the models and the engineers building the hardware to the policymakers crafting regulations and the end-users operating the machines—to prioritize security as a core component of design, not an optional feature. The concerted efforts that followed aimed to ensure that the integration of humanoid robots into society would be both innovative and fundamentally safe, preventing the silent whispers of control from ever escalating into a roar of widespread disruption.