Introduction to a Dual-Edged Technology
In an era where cross-platform compatibility drives innovation, the seamless integration of Linux virtual machines (VMs) within Windows environments stands out as a remarkable achievement, with over 60% of developers reportedly leveraging such setups for testing and development. This technology, once a niche solution, has evolved into a cornerstone of modern computing, enabling professionals to harness the strengths of both operating systems on a single device. The ability to run a lightweight Linux distribution alongside Windows sparks curiosity about its potential—yet it also raises questions about hidden risks in this powerful fusion.
This integration serves a critical purpose by bridging the gap between two dominant operating systems, offering flexibility for software creation and system administration. Beyond legitimate use, however, a darker side emerges as cyber threat actors exploit this same technology for stealthy operations. The following review delves into the capabilities, applications, and challenges of Linux VMs in Windows, shedding light on their dual nature as both a productivity tool and a potential security vulnerability.
Technical Underpinnings of Virtualization
Hyper-V as the Backbone
At the heart of running Linux VMs on Windows lies Microsoft’s Hyper-V, a robust virtualization platform that simplifies the deployment of virtual environments directly from a Windows host. This technology allows users to create and manage VMs with minimal overhead, supporting a range of Linux distributions tailored for efficiency. Setting up Hyper-V is straightforward, often requiring just a few configuration steps to enable the feature and allocate resources for a guest operating system.
Performance remains a key consideration, especially when utilizing lightweight distributions like Alpine Linux, which demands as little as 120MB of disk space and 256MB of memory. Such minimal resource usage ensures that the host system experiences negligible impact, making Hyper-V an attractive option for multitasking across platforms. This efficiency empowers users to run multiple VMs without sacrificing the responsiveness of their primary Windows environment.
Bridging Platforms and Purposes
The compatibility offered by Linux VMs on Windows hosts facilitates a wide array of use cases, particularly in cross-platform development and testing scenarios. Developers can simulate diverse environments to ensure software functionality across operating systems, while IT professionals use these setups for server simulations and network configurations. This versatility eliminates the need for separate hardware, streamlining workflows in tech-heavy industries.
Yet, this same compatibility opens doors for misuse, as malicious actors leverage isolated VM environments to evade detection. By hiding activities within a Linux guest system, threat actors can bypass security measures focused on Windows, exploiting a blind spot in traditional defenses. This duality underscores the importance of understanding both the benefits and the risks inherent in such powerful tools.
Cyber Threats Adapting to Virtualization
Recent trends reveal a concerning shift as cyber threat groups adopt Linux VMs for espionage and evasion purposes. Notably, a pro-Russian group dubbed Curly Comrades has been observed using these virtual environments to maintain covert access within targeted networks. Their approach focuses on long-term persistence rather than immediate disruption, highlighting a strategic intent aligned with broader geopolitical motives.
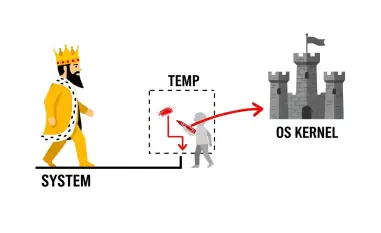
A significant tactic involves deploying minimalistic Linux VMs to isolate command-and-control (C2) operations, effectively shielding malicious activities from endpoint detection and response (EDR) tools. By routing traffic through the host IP address, such operations blend into legitimate network behavior, complicating efforts to identify threats. This innovative misuse of virtualization technology signals an evolution in attacker strategies, challenging conventional security paradigms.
Practical Uses and Shadowy Exploits
Across industries like software development and system administration, Linux VMs in Windows environments are indispensable for tasks such as debugging code and managing server configurations. Tech companies rely on these setups to ensure applications perform consistently across platforms, while educational institutions use them to teach operating system concepts. The accessibility of virtualization enhances productivity by consolidating diverse tools into a single system.
On the flip side, malicious implementations reveal a stark contrast, with groups like Curly Comrades exploiting Alpine Linux VMs to host custom malware. Tools such as CurlyShell, a reverse shell for persistent C2 communication, and CurlCat, a reverse proxy for traffic tunneling, exemplify how minimalistic environments can harbor sophisticated threats. These stealthy operations underscore the potential for legitimate technology to be weaponized in unexpected ways.
The contrast between beneficial and harmful applications illustrates a broader tension in cybersecurity. While organizations reap efficiency gains from virtualization, adversaries capitalize on the same isolation to conceal their tracks. This dichotomy necessitates a deeper examination of how such technologies are deployed and monitored in real-world settings.
Security Hurdles in Isolated Environments
Securing Linux VMs within Windows systems presents formidable challenges, primarily due to the difficulty of detecting malicious behavior in isolated environments. Traditional EDR solutions, often tailored for Windows-centric threats, struggle to monitor activities within a Linux guest OS, leaving a gap in visibility. This limitation allows threat actors to operate undetected for extended periods.
Further complicating the issue is the technical hurdle of adapting security tools to cover cross-platform scenarios. Many existing defenses lack the capability to inspect VM traffic or identify anomalies in lightweight distributions, creating a blind spot for IT teams. Addressing this requires a shift toward broader monitoring strategies that encompass both host and guest environments.
The evolving nature of threats exploiting virtualization also demands innovative approaches to system hardening. Without proactive measures, organizations risk overlooking subtle indicators of compromise, such as abnormal authentication patterns or unauthorized VM creation. This underscores the urgency of rethinking security frameworks to keep pace with sophisticated adversaries.
Looking Ahead at Virtualization Trends
Advancements in virtualization technology hold promise for enhancing the functionality and security of Linux VMs on Windows hosts. Emerging tools and features aim to improve resource allocation and integration, potentially offering built-in safeguards against misuse. Over the next few years, from 2025 to 2027, expect developments that prioritize seamless cross-platform monitoring to address current vulnerabilities.
However, the increasing adoption of such technology by threat actors remains a looming concern, as adversaries continue to refine evasion tactics. This trend suggests a future where cybersecurity solutions must evolve rapidly, incorporating machine learning and behavioral analysis to detect anomalies within VMs. Staying ahead of these challenges will require collaboration between technology providers and security experts.
The trajectory of this technology also points toward greater emphasis on user education and policy enforcement. Organizations will need to balance the benefits of virtualization with stringent access controls to prevent unauthorized deployments. Anticipating these shifts is crucial for maintaining a secure digital landscape amid growing complexities.
Final Reflections and Path Forward
Reflecting on this review, the exploration of Linux VMs in Windows environments revealed a technology that excels in bridging operational gaps but also exposes critical security flaws when exploited by malicious entities. The balance between productivity and risk stood out as a defining theme, with real-world applications showcasing both innovative uses and alarming misuses by groups like Curly Comrades.
Moving forward, organizations need to prioritize the development of multilayered defense strategies that extend beyond traditional EDR tools, focusing on network traffic analysis and proactive system hardening. Investing in training for IT staff to recognize signs of VM misuse becomes essential, as does the adoption of integrated security platforms capable of monitoring diverse environments. These steps offer a practical roadmap to mitigate risks while preserving the advantages of virtualization technology.