As the United Kingdom forges ahead with its ambitious Cyber Security and Resilience Bill, a critical dialogue has opened between lawmakers and the cybersecurity professionals who will navigate its real-world implications. This landmark legislation, designed to replace the 2018 NIS Regulations with a more robust, NIS2-inspired framework, has successfully passed its second parliamentary reading and now enters the crucial committee stage. During this period of detailed scrutiny, the Public Bill Committee has extended an open invitation for written evidence from industry experts, creating a pivotal opportunity to infuse the bill with practical, frontline knowledge. With broad political consensus supporting its objectives, the focus shifts from whether the bill should exist to how it can be refined into an effective, workable, and future-proof defense for the nation’s most vital digital infrastructure. The outcome of this collaborative effort, expected to culminate in Royal Assent later this year, will determine the future of UK cybersecurity for years to come.
Scrutinizing the Framework
Expanding the Digital Defense Perimeter
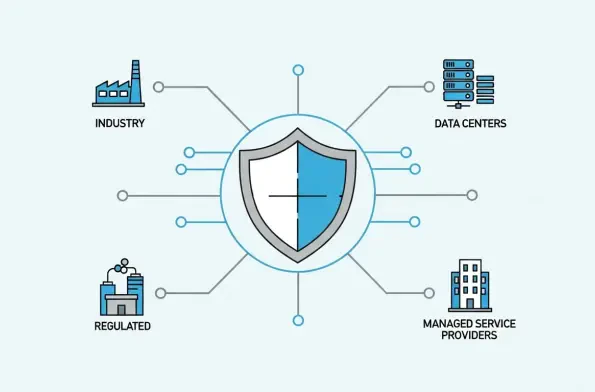
A cornerstone of the proposed legislation is its significant expansion of regulatory scope, drawing a wider circle of digital service providers under its purview and acknowledging the deeply interconnected nature of modern infrastructure. The bill extends its reach to previously excluded but critical entities, most notably Managed Service Providers (MSPs), which are often deeply embedded in the IT operations of countless organizations. By including MSPs, the legislation recognizes that a compromise at the provider level can have a cascading impact across numerous clients. Similarly, the inclusion of data centers and large load controllers, such as the rapidly proliferating electric vehicle charging points, reflects a forward-looking approach to security. These entities represent potential single points of failure and high-value targets for malicious actors seeking to disrupt essential services or access sensitive information. This broadening of the definition of critical infrastructure aims to close security gaps that have emerged as technology has evolved, ensuring that the regulations are comprehensive enough to protect the foundational services upon which the UK’s economy and society depend.
The legislation moves beyond merely identifying more entities to regulate; it also introduces far more stringent and prescriptive obligations for how they must operate and respond to cyber threats. A key change involves the rules for incident reporting, which are set to become much stricter, with tighter timelines for disclosure and a broader definition of what qualifies as a reportable event. This shift is intended to provide regulators with a more immediate and complete picture of the national threat landscape, enabling faster coordinated responses. Furthermore, the bill places a new and explicit mandate on in-scope organizations to proactively manage their supply chain risks. This requirement forces a deeper level of due diligence, compelling companies to look beyond their own firewalls and assess the security posture of their vendors and partners. To guide these efforts, the bill stipulates adherence to “proportionate and up-to-date security requirements,” which will be benchmarked against the National Cyber Security Centre’s (NCSC) comprehensive Cyber Assessment Framework (CAF), creating a standardized measure of resilience across diverse sectors.
Strengthening Regulatory Oversight
To ensure that these new mandates are met with meaningful action, the Cyber Security and Resilience Bill grants regulators significantly enhanced enforcement powers, signaling a move toward a more assertive and punitive compliance regime. The framework is designed to give regulatory bodies the teeth they need to hold organizations accountable for security failings. A central feature of this strengthened authority is the potential for substantially higher financial penalties for non-compliance. This approach mirrors trends seen in other data protection and security regulations, where the risk of severe monetary fines serves as a powerful incentive for organizations to invest in robust cybersecurity measures and foster a culture of security from the top down. These elevated enforcement capabilities are not merely punitive; they are intended to drive a fundamental shift in how critical infrastructure providers prioritize and manage cyber risk, transforming it from an IT issue into a core business imperative that receives board-level attention and resources. The ultimate goal is to create a deterrent strong enough to compel proactive defense rather than reactive cleanup.
The bill codifies the NCSC’s Cyber Assessment Framework (CAF) as the definitive standard for evaluating the security and resilience of critical national infrastructure. This move provides a clear, structured, and consistent methodology for both organizations and regulators to follow, replacing what could otherwise be a fragmented or subjective set of expectations. The CAF is designed to be outcome-focused, allowing organizations a degree of flexibility in how they achieve the required security objectives while still ensuring a high baseline of protection. It covers a wide range of security principles, from governance and risk management to data security and incident response. By mandating adherence to this framework, the legislation aims to create a common language and a unified standard for cybersecurity across all in-scope sectors. This standardization is crucial for establishing clear benchmarks, facilitating effective regulatory audits, and enabling organizations to demonstrate their compliance in a transparent and measurable way, ultimately raising the overall security posture of the nation.
The Devil in the Details
The Call for Clarity and Precision
Despite the bill’s clear high-level objectives, a significant concern among industry experts is the amount of crucial operational detail that remains undefined in the primary text. A prevailing view is that the true substance of the legislation—the specific rules that will govern day-to-day compliance—will be determined later through secondary legislation. This deferred approach leaves many critical questions unanswered at this stage. For instance, the bill lacks precise definitions for key terms such as “critical suppliers” and “managed services,” creating uncertainty for businesses trying to determine if they fall within its scope. Similarly, the specific thresholds that would trigger a mandatory incident report are not yet established. This ambiguity makes it challenging for organizations to begin preparing for compliance, as the full extent of their obligations is still unknown. Experts caution that without clearer, more concrete definitions embedded within the bill itself, there is a risk of inconsistent interpretation and application, potentially undermining the legislation’s effectiveness.
In response to this legislative ambiguity, cybersecurity professionals are advocating for a more refined and practical approach to be incorporated as the bill moves forward. A central demand is for the development of clear, risk-based definitions that would help organizations better understand their specific compliance responsibilities. A risk-based model would ensure that the most stringent requirements are applied to the most critical systems, preventing a one-size-fits-all approach that could place an undue burden on lower-risk entities. Furthermore, there is a strong push for a more streamlined incident reporting mechanism. Experts warn that overly broad reporting criteria could lead to “over-reporting” of minor or inconsequential events, creating a deluge of data that would overwhelm regulators and dilute their focus on genuine, high-impact threats. The goal is to design a system that captures critical threat intelligence without creating unnecessary administrative noise, allowing security teams and regulatory bodies to concentrate their resources where they are most needed.
Ensuring Practical and Consistent Application
A significant operational challenge highlighted by industry stakeholders is the need for consistency across the various regulatory bodies that will be tasked with enforcing the new bill. Many organizations, particularly those operating in multiple sectors, are already subject to oversight from several different regulators, each with its own set of rules and reporting requirements. There is a palpable concern that if the implementation of the Cyber Security and Resilience Bill is not carefully coordinated, it could introduce yet another layer of duplicative compliance burdens. Businesses fear a scenario where they are forced to report the same incident to multiple agencies in different formats or adhere to conflicting security directives. To prevent this, experts are calling for the establishment of a clear framework for inter-regulatory collaboration. This would ensure that guidance is harmonized, reporting is streamlined through a “report once, share many” principle, and enforcement actions are applied consistently, thereby reducing complexity and allowing organizations to focus on improving their security posture rather than navigating a maze of bureaucracy.
Beyond regulatory harmonization, there is a pressing need to establish transparent and effective information-sharing mechanisms that can bolster national resilience without compromising sensitive commercial data. While the goal of enhanced incident reporting is to provide the government with a clearer view of the threat landscape, organizations are understandably cautious about sharing proprietary information or details of security vulnerabilities that could be exploited by competitors or adversaries if not handled properly. The consultation process has underscored the importance of creating trusted, secure channels for this information exchange. Experts are proposing models that would allow for the anonymization of certain data and provide clear legal protections for organizations that report incidents in good faith. An effective framework would foster a two-way street, where the government not only collects data but also shares actionable threat intelligence back with the industry, creating a collaborative ecosystem that strengthens the security of all participants and enhances the UK’s collective defense against sophisticated cyber threats.
A Collaborative Path Forward
The extensive consultation process revealed a shared understanding that while the legislative framework provided a necessary foundation, its ultimate success hinged on the practical details ironed out through expert feedback. The dialogue between Parliament and the cybersecurity community was instrumental in highlighting the operational realities that the bill needed to address. Concerns over ambiguous definitions, the potential for regulatory overlap, and the risk of inefficient reporting systems were brought to the forefront, prompting a more nuanced and detailed examination of the bill’s text. This period of scrutiny ensured that the final legislation was not merely a top-down mandate but a collaboratively shaped instrument, better equipped to handle the dynamic and complex nature of modern cyber threats. The engagement demonstrated that for such a critical piece of national security legislation to be truly effective, it required the integration of frontline experience, which ultimately led to a more practical, resilient, and well-grounded law.