Introduction
A seemingly harmless software uninstallation process can become the unlocked back door for an attacker, a reality recently underscored by a critical vulnerability discovered within the widely used JumpCloud platform. The platform, a cornerstone of IT management for thousands of businesses, was found to contain a flaw that could turn a routine administrative task into a catastrophic security breach. This article aims to dissect this specific vulnerability, known as CVE-2025-34352, to provide a clear understanding of its mechanics, the potential for a complete system compromise, and the essential steps required for mitigation. Readers will gain insight into how a low-privileged user could exploit this issue to gain ultimate control over a Windows system.
Key Questions and Topics
What Is the Core Vulnerability in JumpCloud
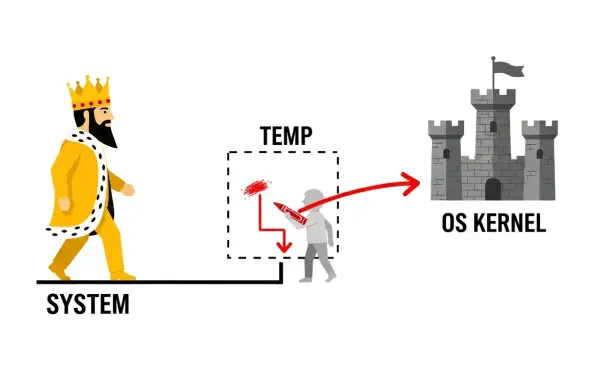
The issue at the heart of this security concern resides within the JumpCloud Remote Assist agent for Windows, a tool designed to provide administrators with remote access for support and management. The vulnerability is not in the agent’s primary operation but rather in its uninstallation logic. When the main agent is removed, it initiates a secondary process to uninstall the Remote Assist component, which unfortunately carries out its tasks in a fundamentally insecure manner.
This secondary uninstaller executes file operations—such as writing, deleting, and running files—with the highest level of system privileges, known as NT AUTHORITY\SYSTEM. However, it performs these powerful actions within the %TEMP% directory, a temporary folder that is, by design, writable by any user on the system. This combination of elevated permissions operating in a low-security, user-controlled environment creates a perfect storm for exploitation, as the process inherently trusts a location that should never be trusted.
How Can This Flaw Be Exploited
An attacker with only low-level local access to a machine can leverage this flaw through a technique known as a link-following attack. Because the uninstaller uses predictable file names in the insecure %TEMP% directory, an attacker can anticipate its actions. The attacker can then create a symbolic link or a directory junction point, which essentially acts as a redirect, tricking the uninstaller into performing its high-privilege actions on a different, protected part of the system.
For instance, instead of deleting a temporary file as intended, the uninstaller could be redirected to delete a critical system driver or an essential operating system file located in the Windows directory. Similarly, a file-write operation could be manipulated to plant a malicious executable in a protected folder. This allows a user with minimal permissions to effectively command a SYSTEM-level process to compromise the integrity of the entire operating system on their behalf.
What Are the Potential Consequences of an Attack
The impact of successfully exploiting this vulnerability ranges from disruptive to completely devastating. In one scenario demonstrated by security researchers, an attacker could use the flaw to corrupt or delete crucial Windows drivers. This action would lead to immediate system instability, resulting in repeated blue screen crashes and rendering the machine unusable—a classic denial-of-service (DoS) attack that halts productivity and requires significant IT intervention to resolve.
Moreover, the flaw can be escalated beyond simple disruption to achieve a full system takeover. By strategically redirecting the uninstaller’s file operations, an attacker can methodically delete protected system directories or write malicious code to privileged locations. The ultimate goal of such an attack is to gain a persistent command shell with NT AUTHORITY\SYSTEM privileges. At that point, the attacker has complete control over the device, enabling them to install malware, exfiltrate data, and move laterally across the network.
Who Is at Risk and What Is the Solution
Given that JumpCloud’s platform is utilized by over 180,000 organizations worldwide, the potential attack surface is significant. Any Windows device managed by JumpCloud running an agent version released before 0.317.0 is exposed to this local privilege escalation vulnerability. The risk is present for any organization that allows users, even those with standard permissions, to log into these managed systems.
Following a responsible disclosure from the cybersecurity researchers at XM Cyber who discovered the flaw, JumpCloud swiftly validated the findings and released a patched version of the agent. The primary and most effective mitigation is for administrators to ensure that all managed Windows endpoints are updated to agent version 0.317.0 or a later release. This update corrects the uninstaller’s behavior by preventing it from performing privileged operations within insecure, user-writable directories, thereby closing the door on this attack vector.
Summary
This vulnerability in the JumpCloud agent serves as a critical reminder of a core security principle: processes with elevated privileges must never interact with user-writable locations without first securing them. The flaw, identified as CVE-2025-34352, clearly demonstrates how a privileged uninstaller operating in the %TEMP% directory creates a direct pathway for local privilege escalation. The consequences, which range from denial-of-service to a complete system compromise, highlight the urgency for all affected organizations to apply the security patch.
Final Thoughts
The incident served as a powerful lesson on the subtle but significant attack surfaces that can exist within trusted IT management software. The responsible disclosure and rapid remediation of this flaw prevented what could have been widespread exploitation, underscoring the value of proactive security research. For system administrators, the event reinforced the foundational concept that the intersection of high privilege and insecure environments is a danger zone that demands explicit hardening, such as modifying a folder’s Access Control Lists (ACLs) before performing sensitive operations.