
Kristen Papadaikis
Security AdvisorKristen Papadaikis lends her expertise on business perspectives to security specialists. She offers tangible advice on maintaining robust security measures for businesses operating with remote or hybrid workforces, which has proven essential for staying ahead in a post-pandemic environment. Kristen’s work has been instrumental in helping companies stay ahead of security threats as the business landscape changes.
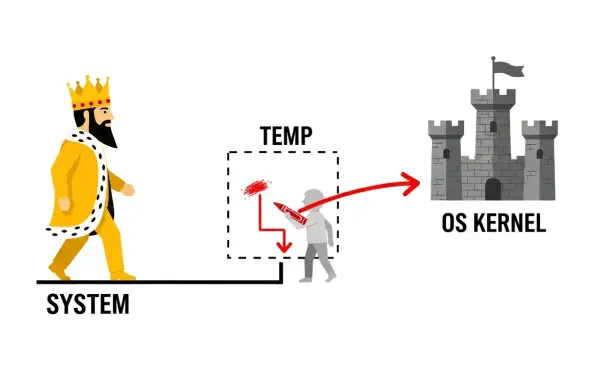
Introduction A seemingly harmless software uninstallation process can become the unlocked back door for an attacker, a reality recently underscored by a critical vulnerability discovered within the widely used JumpCloud platform. The platform, a cornerstone of IT management for thousands of
The relentless cascade of high-profile security breaches throughout 2025 transformed the global conversation around digital risk, solidifying the year as a watershed moment for cybersecurity. An unprecedented volume of sophisticated intrusions targeted major enterprises and household brands,

Introduction The sophisticated landscape of modern cyber threats has evolved to a point where attackers are not just trying to sneak past security systems, but are actively turning trusted components of those systems against them. This advanced evasion tactic, known as a Bring Your Own Vulnerable

As sophisticated digital scams continue to bleed billions from the UK economy and devastate individual finances, the nation's chief financial watchdog has responded with a new weapon in the consumer's arsenal. The Financial Conduct Authority (FCA) recently launched its "Firm

AI-Driven Identity Security is no longer a futuristic concept but a present-day necessity, representing a pivotal advancement in how enterprises protect their most critical assets. This review explores the evolution of this technology, dissects its core features and performance capabilities, and
In 2025, cyber threats from nation-states have become more active, aggressive, and advanced. Unlike regular cybercriminals, these state-sponsored actors often have long-term goals. They aim to steal valuable intellectual property, gather intelligence for political or military reasons, and influence

With years of experience defending multinational corporations from digital threats, Malik Haidar has a unique vantage point on the intersection of business strategy and cybersecurity. We sat down with him to dissect the recent Marquis Software Solutions breach, a case that serves as a powerful

Our Picks
